
 |
 |
 |

C Y B E R C I T Y O N L I N E |
Protection against Spyware, Trojan Horses & Viruses
Spyware and its Protection
Spyware and other unwanted software refers to software that performs certain tasks on your computer, typically without your consent. This may include giving you advertising or collecting personal information about you. Learn more about the symptoms of spyware and other unwanted software and how you can help protect your computer.
Download Microsoft Windows AntiSpyware (Beta)Get the beta version of our new anti-spyware software to help protect your PC from spyware and other potentially unwanted software.
CommunityHave a question? Get answers from experts and other community members.Security at Home Community
Windows AntiSpyware (Beta) newsgroupSpyware Removal
Detect and remove unwanted software from your computer.
Lavasoft Ad-aware No charge
Spybot Search & Destroy (S&D) No chargeImportant: Makers of spyware and other unwanted software might disguise their programs as anti-spyware tools. Click the links to the programs above or ask someone you trust to recommend a tool before you download and install it.
The Basics of Trojans
The "Trojan horse" applications discussed within this website are remote administration "hacker" utilities that will allow a user to control another user's computer across the Internet using the "client/server" approach. Trojan horse applications can provide equal, if not more control of a remote PC system than the person sitting at its keyboard.Definitions
"Trojan"
- A Trojan (or a Trojan horse) is a destructive program that masquerades as a benign application. Unlike viruses, Trojan horses do not replicate themselves but they can be just as destructive."hacker"
- "Hacker" is a slang term for a computer enthusiast. Among professional programmers, the term hacker implies an amateur or a programmer who lacks formal training. Depending on how it used, the term can be either complimentary or derogatory, although it is developing an increasingly derogatory connotation."client/server" approach
- A client is defined as a requester of services and a server is defined as the provider of services."IP Address" (Internet Protocol Address)
- The address of a computer attached to a TCP/IP network (e.g. the Internet). Every client and server must have a unique IP address. Client workstations have either a permanent address or one that is dynamically assigned to them each dial-up session. IP addresses are written as four sets of numbers separated by periods; for example, 192.168.111.222
"port"
- In an TCP/IP network (e.g. the Internet), a port represents an endpoint in the establishment of a connection between computers. For the computer that acts as the server, the port number will typically identify the type of service it is. For example, TCP port 80 is used for HTTP, TCP port 21 is used for FTP, and TCP port 25 is used for SMTP . It should be noted that there are 65,535 (64K) port numbers!
Which PC's can be affected?
Depending on the trojan involved, they're designed to affect Windows 95/98 PC's, Windows NT PC's, or both.
How do the trojans work?
How a hacker establishes the connection to another user's computer, is that the hacker running the "client" portion establishes a connection to the IP address of a known PC that has the "server" portion installed upon itIf the hacker running the "client" portion doesn't know the IP address of the user's PC which has been compromised by the "server" portion. The hacker usually initiates a series of connections to a large range of IP addresses on the Internet (known as "scanning"), looking for any PC that responds back to the attempt. If a PC responds back, it responds with its IP address. Then all the hacker has to do, is to establish a connection to that IP address.
Keep in mind that 99% of the time, the hacker doesn't have a specific target (or victim) to begin with, so any PC that answers back to their attempted connections satisfy their goal of hacking into another's PC.
Because the "server" portion is configured to use (or "listen" on) a particular port number, it's the client who attempts a connection to that specific port number to initiate the connection between computers.
NOTE: Some trojans may use more than one port number. This is because one port is used for "listening" and the other/s are used for the transfer of data.
In their default configurations, the following trojans use:
Back Orifice - UDP port 31337 or 31338
Deep Throat - UDP port 2140 and 3150
NetBus - TCP port 12345 and 12346
Whack-a-mole - TCP port 12361 and 12362
NetBus 2 Pro - TCP port 20034
GirlFriend - TCP port 21544
Sockets de Troie - TCP port 5000, 5001 or 50505
Masters Paradise - TCP port 3129, 40421, 40422, 40423 and 40426Devil - port 65000
Evil FTP - port 23456
GateCrasher - port 6969
Hackers Paradise - port 456
ICKiller - port 7789
ICQTrojan - port 4590
Phineas Phucker - port 2801
Remote Grab - port 7000
Remote Windows Shutdown - port 53001There have been several reports of ICQ users being compromised via the ability to send files to/from one another. I strongly suggest that you click here to read ICQ's latest End User Agreement, which discusses this topic.
The best defense to prevent your PC from becoming compromised by these or any other trojans, is to not download files from unknown sources!Acquire an antivirus software product.
Believe it or not, the major players (McAfee AntiVirus, Norton AntiVirus, Command AntiVirus, etc.) in the AV market are including the ability for their software to detect a static string of code within each trojan. Therefore, I'd strongly suggest insuring that you keep up-to-date with your virus signature files. If your AV product does not detect these trojans, send an email to the mfg'r and request that they do.
The best method for Trojan Detection:
Author's email address is dkelloway@commodon.com and URL
To determine if your system has been compromised, but it requires that you:
A. have a basic understanding of the state of an "active connection" and
B. that you're familiar with the port numbers commonly used by the trojans.
With regards to the state of an "active connection". There are several types, but there's really only one type that you need to know about.
The "listening" state - which is when your PC listens on a port number, awaiting for another PC to make a connection to it. The "listening state" is the state that the trojan will be in after your system is rebooted.
NOTE: Some trojans may use more than one port number. This is because one port is used for "listening" and the other/s are used for the transfer of data.The following ports used In the default configurations of Trojans:Back Orifice - UDP port 31337 or 31338
Deep Throat - UDP port 2140 and 3150
NetBus - TCP port 12345 and 12346
Whack-a-mole - TCP port 12361 and 12362
NetBus 2 Pro - TCP port 20034
GirlFriend - TCP port 21544
Sockets de Troie - TCP port 5000, 5001 or 50505
Masters Paradise - TCP port 3129, 40421, 40422, 40423 and 40426
Devil - port 65000
Evil FTP - port 23456
GateCrasher - port 6969
Hackers Paradise - port 456
ICKiller - port 7789
ICQTrojan - port 4590
Phineas Phucker - port 2801
Remote Grab - port 7000
Remote Windows Shutdown - port 53001If you know of another Trojan (and/or a corrections) to add to the above, please mail the webmaster.
How to detectIf after following the directions outlined further down below, you've determined that your PC is "listening" on any of the above ports. It's a very strong indicator that your PC has been compromised. Click the appropriate link to learn how to remove the trojan involved.
Important Notes:
Although Back Orifice and NetBus are commonly found to be configured to use their default port/s in establishing the connection between the client and server, they have been found to be configured to use different port/s.
Regardless what port/s they may be configured to use, the important thing to know is that if your a home user (and your PC doesn't participate on a LAN or a SoHo LAN), your PC shouldn't be "listening" on any port (or ports) after it's been rebooted.
Keep in mind that for some PC's that are connected to a LAN or a SoHo LAN, it is common for certain ports (137,138 and 139) to be listening. Such ports are used for NetBIOS, and sometimes port 135 (RPC) may be used as well.
How to determine what ports are "listening"Perform the following steps:
Step 1. - Reboot your PC. Do NOT establish a dial-up connection.
Click Start | Shut Down
Click Restart
Click OK
Step 2. - After you reboot your PC and before doing anything else, open a DOS window.
Click Start | Programs | MS-DOS Prompt
NOTE: If you don't have a shortcut to the MS-DOS Prompt, don't worry. You can
Click Start | Run
Type command
Click OK
Step 3. - Type "netstat -an >>c:\netstat.txt" (without the quotes)
Type netstat -an >>c:\netstat.txt
Press ENTER
Step 4. - Close the DOS window.
Type exit
Press ENTER
Step 5. - Open Explorer
Click Start | Programs | Windows Explorer
Step 6. - Change to the C drive and double click on the netstat.txt file. It should open with NOTEPAD.
Click (C:)
Double-click netstat.txt
Step 7.
Look under the "Local Address" column and examine the port numbers for any connection found to be in a "listening" state.
For reference, the port numbers are shown as ":XXXXX" to the right of the IP address, where "XXXXX" is a 1 to 5 digit number.
Provided below are some examples of what you may might find:
The above example is typical of a home user's PC. The system (after a reboot) doesn't show any active connections. If your system looks like this, then congratulations! You have nothing to worry about.
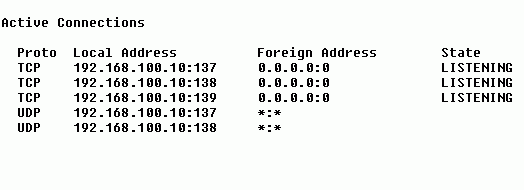
The above example is typical of a PC on a LAN. The system (after a reboot) shows several connections in a listening state, used by NetBIOS. As mentioned above, the ports used by NETBIOS are ports 137 (nbname), 138 (nbdata) and 139 (nbsession).Again, if your system isn't showing any active connections other than the ones related to using NetBIOS, then congratulations! You have nothing to worry about.
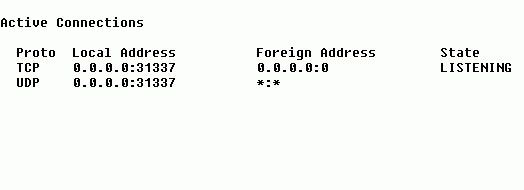
The above example is typical of a home user's PC that's been compromised with the Back Orifice server portion, and whereby it's been configured to use the port 31337 (the default).
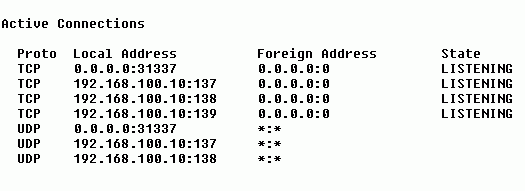
The above example is typical of a PC on a LAN that's been compromised with the Back Orifice server portion, and whereby it's been configured to use port 31337 (the default).
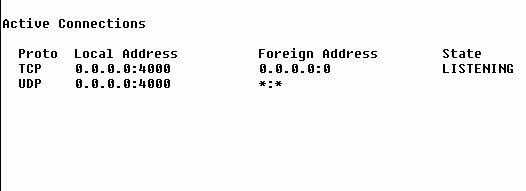
The above example is typical of a home user's PC that's been compromised with the Back Orifice server portion that's been configured to use port 4000 instead of the default 31337.
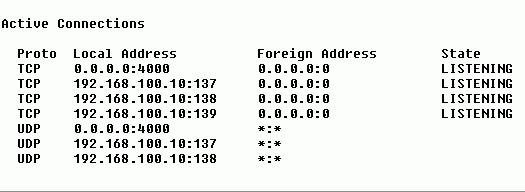
The above example is typical of a PC on a LAN that's been compromised with the Back Orifice server portion that's been configured to use port 4000 instead of the default 31337.
If your system shows any ports in a listening state that you cannot identify or explain. It might be wise to further investigate the possiblity that your system may be compromised with one of these trojans using a different port other than the default/s.
NOTES:
Some ports that may be found in a listening state include:
FTP, which uses TCP port 21
Telnet, which uses TCP port 23
Gopher, which uses TCP port 70
HTTP (a webserver), which uses TCP port 80
If you do find your system "listening" on any of these ports. You should know whether it should or shouldn't be. If it shouldn't be, then it's wise to further investigate the possiblity that your system may be compromised with one of the trojans using a different port other than the default/s.Author's email address is dkelloway@commodon.com and URL
![]() This website discusses remote administration utilities that will allow
a user to control another user's computer across the Internet.
This website discusses remote administration utilities that will allow
a user to control another user's computer across the Internet.
Computer Associates 12-month free trial
F-secure 6-month free trial
McAfee 90-day free trial
Panda Software 90-day free trial
Symantec 90-day free trial
Trend Micro 90-day free trial
Important: Please uninstall any antivirus software you are currently using before installing a new product; having two different programs might cause problems on your computer.
Cleaning Tools
![]() Back Orifice (BO) cleaning tools
Back Orifice (BO) cleaning tools
![]() More on Back Orifice - The first five steps involve editing the Windows
95/98 registry. And although the steps are easy, it is always risky to
meddle with the Windows registry so try it cautiously
More on Back Orifice - The first five steps involve editing the Windows
95/98 registry. And although the steps are easy, it is always risky to
meddle with the Windows registry so try it cautiously
![]() Various cleaning tools.
Various cleaning tools.
![]() Finding BO on your PCs.
Finding BO on your PCs.